
Ensuring your OpenSSL version is up-to-date is essential for maintaining security and compatibility with various software applications.
Here’s a simple guide on how to check the OpenSSL version and update it across different operating systems.
How to Check the OpenSSL Version
Checking the OpenSSL version is a straightforward process that varies slightly depending on your operating system. Below, we’ll cover the steps for Linux, Windows, and Mac systems.
Before you find the OpenSSL version, make sure you have it installed on your system. It typically comes pre-installed on many operating systems, but if not, you may need to install it manually using your system’s package manager.
Check the OpenSSL Version in Linux
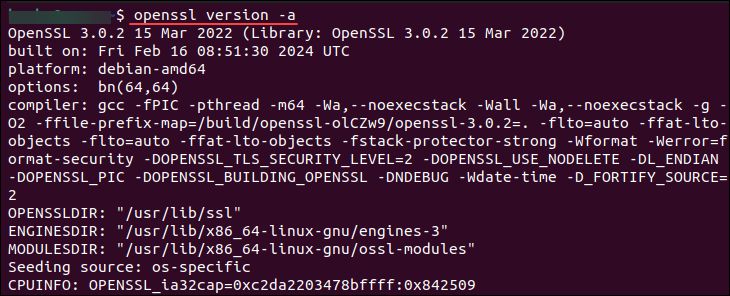
- Access the Terminal: On most Linux distributions, you can access the terminal by pressing Ctrl + Alt + T or searching for “Terminal” in the applications menu.
- Check OpenSSL Version: Once in the terminal, type the following command:
openssl version - This command will display the installed OpenSSL version.
Check the OpenSSL Version in Windows
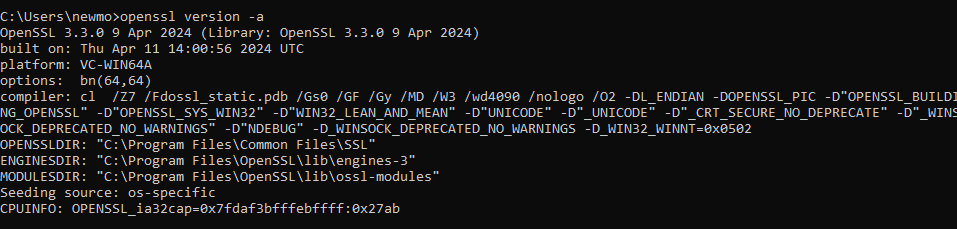
- Access Command Prompt: Press Win + R, type “cmd,” and hit Enter to open the Command Prompt.
- Check OpenSSL Version: In the Command Prompt, enter:
openssl version -a - The prompt will reveal the installed OpenSSL version on your Windows system.
Check the OpenSSL Version on Mac
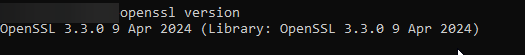
- Access the Terminal: On Mac, you can find the Terminal application in the “Utilities” folder within the “Applications” directory.
- Check OpenSSL Version: Once in the terminal, type:
openssl version - This command will display the OpenSSL version installed on your Mac.
OpenSSL Version Command Flags
You can enhance the “openssl version” command with various flags to extract more information about the OpenSSL installation. For example:
- -a: Displays all information, including compiler details.
- -b: Shows the build date.
- -v: Provides verbose output.
- -h or –help: Displays a list of command-line options and their descriptions.
- -f or –full: Provides detailed information, including library and compiler details.
- -p or –purpose: Shows the default cipher list and what different compiled-in options mean.
- -s or –show: Displays the list of standard directories that OpenSSL uses for configuration files, certificates, and private keys.
- -t or –target: Prints the target platform.
- -d or –shared: Shows whether the OpenSSL library was compiled with shared libraries.
Here’s how you would utilize these flags in the terminal using the -h flag example:
openssl version -h
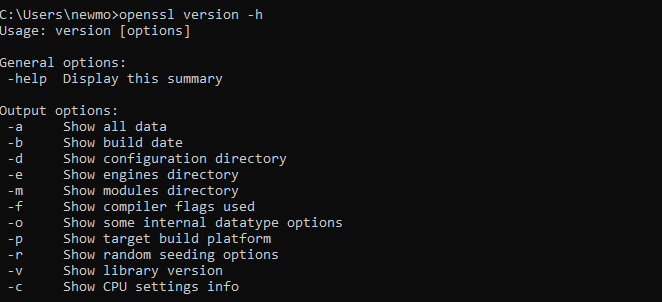
Flags can offer a deeper insight into your OpenSSL installation, helping troubleshoot compatibility checks, and understand the specific configuration of your OpenSSL library.
OpenSSL Version Format
The version output typically follows this format: OpenSSL <version> <date>
- OpenSSL: This is the identifier indicating the software package. It signifies that the version information pertains to OpenSSL.
- <version>: This part denotes the specific version number of OpenSSL. Versions consist of numbers separated by dots (e.g., 1.1.1). Each number represents a different level of update, with major updates typically changing the first number, minor updates changing the second number, and patch updates changing the third number. Sometimes, there might be additional qualifiers such as ‘p’ for patch releases or ‘beta’ for pre-release versions.
- <date>: This indicates when the OpenSSL version was released or built. It helps users understand the age of the software and assess whether it includes recent security patches or features. Dates are typically formatted as month and year (e.g., May 2024).
How to Update to the Latest OpenSSL Version
Updating OpenSSL involves specific steps for each operating system:
Linux
- Update Package Lists: Run the command:
sudo apt update - Upgrade OpenSSL. Execute:
sudo apt upgrade openssl
Windows
- Download Latest Version: Visit the OpenSSL for Windows website and download the latest installer.
- Run Installer: Double-click the downloaded installer and follow the on-screen instructions. You can also check our in-depth article on how to install OpenSSL on Windows.
Mac
- Update Homebrew (if you have it installed): Homebrew is a popular package manager for macOS. If you have Homebrew installed, it’s a convenient way to update OpenSSL. Open a terminal window and run:
brew update - Upgrade OpenSSL using Homebrew: After updating Homebrew, you can upgrade OpenSSL by running the following command:
brew upgrade openssl
If you don’t have Homebrew installed, you can still update OpenSSL manually on your Mac. Here’s how you can do it:
- Download the latest version of OpenSSL: Visit the OpenSSL website and navigate to the “Downloads” section. Download the source code package for the latest version available.
- Extract the downloaded file: Once the download is complete, extract it to the directory where it was downloaded. You can do this by double-clicking the downloaded file or using the tar command in the terminal. For example:
tar -xzvf openssl-.tar.gz - Navigate to the extracted directory: Use the cd command to navigate into the extracted directory:
cd openssl- - Configure, make, and install OpenSSL: Run the following commands one by one to configure, compile, and install OpenSSL:
./configure
make
sudo make install
That’s it! You’ve now updated OpenSSL manually on your Mac.
Bottom Line
Now that you know how to check the OpenSSL version on Linux, Windows, and Mac, you can update it to the latest version using the provided commands. Keeping OpenSSL up-to-date helps protect your system against vulnerabilities and ensures smooth operation with various software applications.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10


