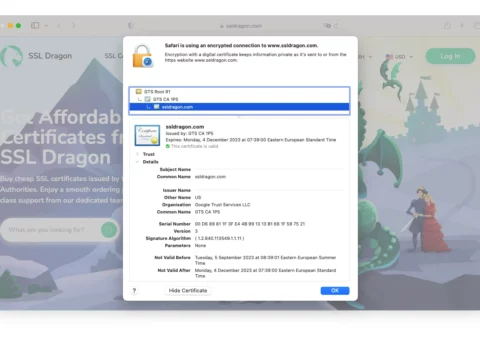
Cipher Suites Explained in Simple Terms: Unlocking the Code
Imagine holding the most complex, intricate key in the digital world – that’s what a cipher suite is to online security! It’s a set of specific algorithms that secure network connections on the internet. You may not know it, but every time you’re online, cipher suites dictate behind the scenes the mechanisms that keep your […]