Mutual TLS (mTLS) is an authentication method that ensures secure communication between both parties in a connection. Unlike regular TLS, which verifies only the server’s identity, mTLS authenticates both client and server by exchanging and validating digital certificates. This approach forms a cornerstone of Zero Trust security frameworks, where nothing is trusted by default.

Whether you’re managing APIs, developing microservices, or securing sensitive business communications, understanding how mTLS works can help protect your valuable data from various threats.
In this article, we’ll guide you through the essentials of mutual TLS authentication, exploring its mechanics, benefits, and practical applications.
Table of Contents
- Understanding TLS
- What is mTLS and How Does It Work?
- TLS vs mTLS: Key Differences Explained
- Why Should You Use mTLS?
- Where Is mTLS Used? Key Implementation Scenarios
- mTLS Implementation: Challenges and Best Practices
- When Not to Use mTLS: Understanding the Limitations
Save 10% on SSL Certificates when ordering from SSL Dragon today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10

Understanding TLS
Transport Layer Security (TLS) is a cryptographic protocol that secures the communication between two applications, typically, a browser and a web server. You encounter TLS whenever you visit a secure website starting with “HTTPS.”
TLS evolved from Secure Sockets Layer (SSL). Although many still refer to these certificates as “SSL certificates,” TLS has replaced SSL as the modern standard after numerous security vulnerabilities were discovered in the original protocol.
When you connect to a secure website, TLS performs three essential security functions:
- Authentication: Verifies the server’s identity using digital certificates issued by trusted Certificate Authorities (CAs).
- Encryption: Creates a secure channel where data remains private, preventing eavesdropping by unauthorized parties.
- Data integrity: Ensures information hasn’t been altered during transmission.
TLS works through a process called a “handshake,” where your browser and the web server exchange information to establish trust and create encryption keys. During this exchange, the server presents its digital certificate for verification.
This certificate contains the server’s public key and details about its identity, all signed by a CA. Your browser checks this signature against its pre-installed list of trusted authorities. If verified, communication proceeds with encryption using session keys generated during the handshake.
This one-way authentication suffices for most everyday web browsing. The website proves its identity to you, but you don’t need to prove yours cryptographically to the site. However, specific sensitive scenarios require stronger security measures, which is where mTLS enters the picture.
What is mTLS and How Does It Work?
Mutual TLS (mTLS), or two-way TLS, takes standard TLS authentication to the next level by requiring both parties to verify each other’s identity through digital certificates. This two-way authentication creates a significantly more secure connection than conventional one-way TLS.
In regular TLS connections, only the server presents a certificate to prove its identity to the client. The client verifies this certificate but doesn’t need to authenticate itself. With mTLS (Mutual Transport Layer Security), both the client and server must present valid certificates during the connection process, establishing stronger trust between them.
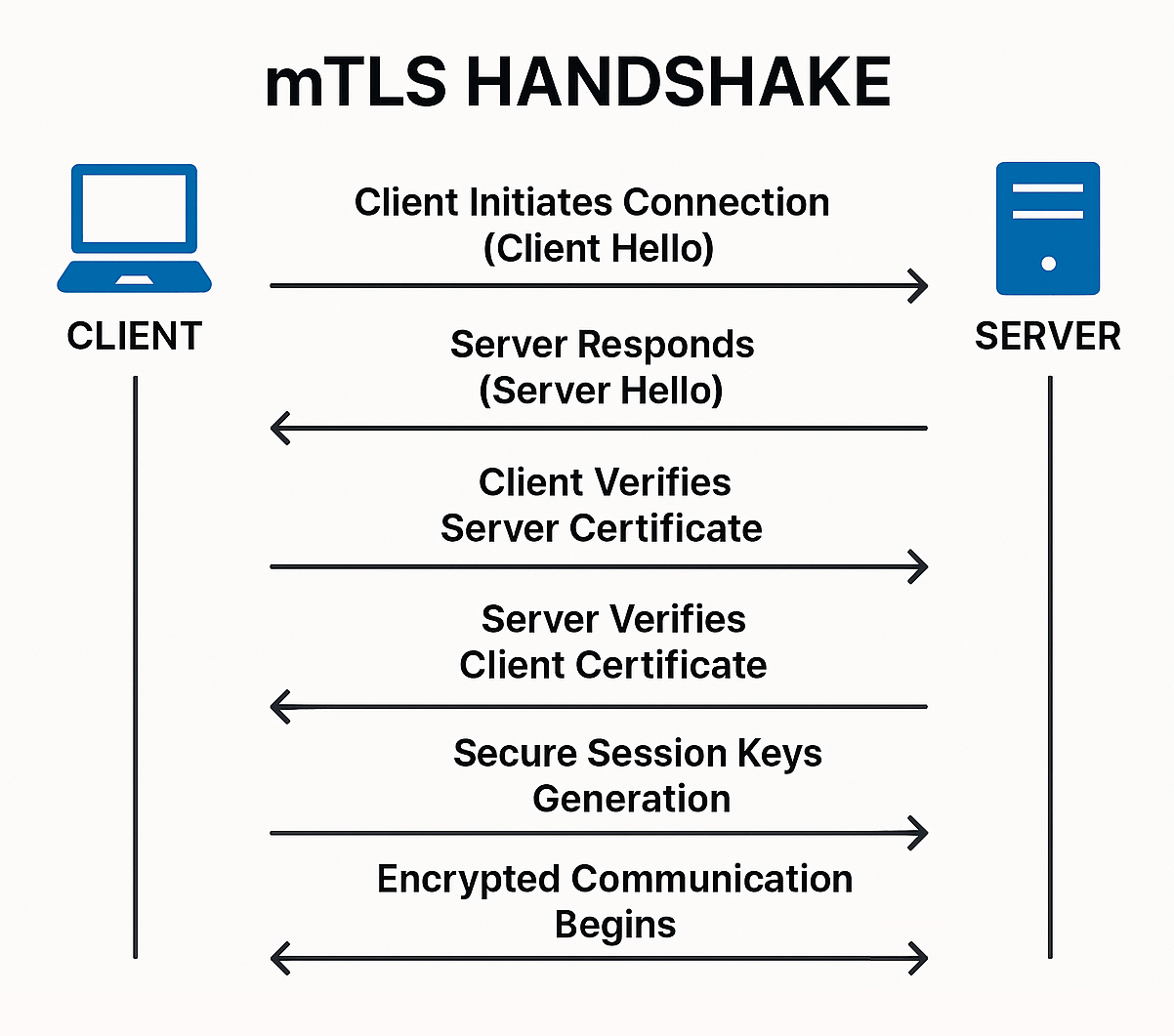
The mTLS Handshake Process
- Step 1: Client Initiates Connection (Client Hello). Your client (for example, a browser or API consumer) initiates a connection request to the server. This request includes the TLS protocol version, cipher suites (the encryption methods it supports), and a random value for generating secure session keys.
- Step 2: Server Responds (Server Hello). The server responds by choosing the highest protocol version supported by both parties and the best-matched cipher suite. It also sends its own random value, a digital server certificate issued by a trusted Certificate Authority (CA), and requests the client’s certificate.
- Step 3: Client Verifies Server Certificate. Your client then checks the server’s certificate to ensure it’s valid, trusted, and truly belongs to the intended server. This verification prevents issues like man-in-the-middle attacks.
- Step 4: Client Sends Certificate. Now, it’s your client’s turn to provide its digital certificate. This client certificate must also come from a trusted CA and include the client’s public key.
- Step 5: Server Verifies Client Certificate. The server examines the client’s certificate carefully. The handshake continues if the server finds the certificate valid and recognizes the client as trustworthy.
- Step 6: Secure Session Keys Generation. Both parties generate secure session keys using their random values. Session keys use symmetric encryption, which speeds up the data transmission once authentication completes.
- Step 7: Encrypted Communication Begins. With mutual authentication successfully completed and session keys established, the client and server start exchanging encrypted data securely.
TLS vs mTLS: Key Differences Explained
While both TLS and mTLS create secure, encrypted connections, several essential distinctions set them apart. Understanding these differences helps determine which protocol best suits your security needs.
1. Direction of Authentication
- Regular TLS: Only authenticates the server’s identity. Your browser or client verifies the server’s digital certificate to ensure it’s genuine and trusted. The server, on the other hand, doesn’t verify your identity at all.
- Mutual TLS: Authenticates both the client and server identities. Your client proves its authenticity to the server by presenting its own certificate, in addition to verifying the server’s identity. This dual verification dramatically improves the security and trust level of the connection.
2. Complexity and Implementation
- Regular TLS: Simpler to set up because only one party (the server) needs a digital certificate. Ideal for websites and public-facing applications where verifying every user’s identity isn’t necessary or feasible.
- Mutual TLS: More complex to implement because both client and server require valid digital certificates issued by a trusted CA. Implementing mTLS involves carefully managing certificate distribution, validation, and lifecycle, especially in dynamic environments like microservices or large-scale APIs.
3. Typical Use Cases
- Regular TLS: Best suited for general internet use, where verifying server authenticity is crucial, but verifying each client individually isn’t practical. Think of public websites, blogs, or online shops.
- Mutual TLS: Essential in scenarios demanding strict security measures, such as internal corporate APIs, microservice-to-microservice communication, client authentication for IoT devices, and regulated industries like finance or healthcare.
4. Security Strength
- Regular TLS: Provides robust protection against common threats such as eavesdropping, man-in-the-middle attacks (server-side), and data tampering. However, it doesn’t prevent unauthorized clients from connecting.
- Mutual TLS: Offers superior security by ensuring only authenticated, authorized clients can access the server. This protection significantly reduces risks associated with spoofing, phishing, brute-force, and other common cyberattacks.
The choice between TLS and mTLS ultimately depends on your specific security requirements and the nature of your application.
Why Should You Use mTLS?
Mutual TLS might initially seem complicated, but once you understand its value, it’s clear why organizations increasingly rely on it. Here are several reasons why using mTLS makes sense for your business:
1. Enhanced Security for Sensitive Communications
mTLS creates a security environment where both connection endpoints verify each other cryptographically. This mutual verification significantly reduces the risk of unauthorized access, making it ideal for transmitting highly sensitive information between services.
Unlike password-based systems that can be compromised through phishing or credential stuffing, certificate-based authentication in mTLS provides more substantial protection. Even if attackers somehow obtain user credentials, they cannot establish a connection without possessing the corresponding private key.
2. Passwordless Authentication
One significant benefit of mTLS comes from eliminating password dependency. Passwords create numerous security vulnerabilities. They can be forgotten, stolen, shared inappropriately, or compromised in data breaches.
Certificate-based authentication removes these password-related risks. Instead of remembering complex passwords, clients use digital certificates securely stored on their devices. This approach reduces friction for users while simultaneously strengthening security.
3. Protection Against Common Attack Vectors
mTLS effectively guards against several dangerous attack types:
- On-path attacks: Prevents attackers from inserting themselves between communicating parties since they cannot present valid certificates.
- Spoofing attacks: Makes impersonating legitimate servers or clients nearly impossible without possessing the appropriate private keys.
- Brute force attacks: Eliminates vulnerability to password guessing attempts since there are no passwords to crack.
- Phishing attempts: Renders credential-stealing attacks ineffective as authentication relies on certificates, not user-supplied credentials.
4. Foundation for Zero Trust Architecture
Zero Trust security operates on the principle of “never trust, always verify.” mTLS aligns perfectly with this model by requiring explicit verification of both parties before allowing communication.
This approach means even internal network traffic gets authenticated and encrypted, limiting lateral movement opportunities for attackers who breach your perimeter. Such certificate-based identity verification forms a cornerstone of modern Zero Trust implementations for organizations seeking robust protection against sophisticated threats.
Save 10% on SSL Certificates when ordering from SSL Dragon today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10

Where Is mTLS Used? Key Implementation Scenarios
Mutual TLS has found its way into various security-conscious environments where strong authentication between machines matters. Let’s explore the primary use cases where this protocol excels.
- Microservices Communication. Modern applications often break into smaller components called microservices, especially when built within Kubernetes. These services communicate constantly, exchanging sensitive data. mTLS ensures each microservice authenticates itself to others, creating a secure environment that prevents unauthorized access or malicious activity.
- API and Internal Service Security. When your APIs handle sensitive operations or critical information, you can’t rely solely on traditional authentication methods. Mutual TLS is frequently adopted for internal APIs to verify clients and enforce strict access control. Companies like Mastercard use mutual TLS to protect developer APIs, ensuring only authenticated parties gain access.
- Business-to-Business (B2B) Secure Data Exchange. Businesses regularly exchange confidential data, from financial details to healthcare records. Mutual TLS ensures both organizations involved verify each other’s identity clearly, providing security beyond traditional passwords or tokens. Industries subject to heavy regulation, such as banking and healthcare, commonly adopt mTLS to comply with stringent security standards.
- Internet of Things (IoT) Device Authentication. IoT devices often operate remotely, performing crucial tasks that require robust security. Whether it’s remote sensors, smart home devices, or payment terminals, mTLS ensures devices communicate exclusively with verified endpoints. By authenticating devices through digital certificates, mutual TLS helps you prevent unauthorized connections or tampering.
- Compliance-Driven Industries. Specific industries, like healthcare, finance, or government, have strict regulations demanding strong authentication and encryption. Mutual TLS fits perfectly into these scenarios, assisting your organization in meeting standards like PCI DSS or HIPAA by authenticating both ends of every secure connection.
mTLS Implementation: Challenges and Best Practices
While mutual TLS provides robust security benefits, implementing it effectively requires overcoming several challenges. Let’s explore these obstacles and the best practices to address them.
1. Certificate Lifecycle Management
Challenge: Perhaps the most demanding aspect of mTLS involves managing the complete certificate lifecycle across your infrastructure. As your environment grows, manual certificate management becomes increasingly burdensome, leading to potential outages when certificates expire unexpectedly.
Solution: Implement certificate management tools or services specifically designed to automate the entire lifecycle:
- Generate private keys using OpenSSL or similar tools
- Create Certificate Signing Requests (CSRs) for each entity needing authentication
- Submit CSRs to your trusted Certificate Authority
- Automate the distribution and installation of signed certificates
- Schedule regular rotation of certificates before expiration
2. Scalability in Dynamic Environments
Challenge: Modern cloud-native environments create unique challenges for mTLS. With containers and microservices constantly spinning up and down, static certificate assignment becomes impractical, especially in Kubernetes deployments where pods may live for just minutes.
Solution: Leverage service mesh technologies that handle certificate management automatically:
- Istio: Provides automatic certificate provisioning, rotation, and authentication for all workloads
- Linkerd: Offers transparent encryption without application code changes and more straightforward configuration
- Custom solutions: Implement orchestration tools that manage certificates as part of your deployment pipeline
3. Trust Anchors and CA Hierarchy
Challenge: Establishing and maintaining proper certificate authority hierarchies requires careful planning. Misconfigurations or weak CA setups can seriously undermine your security posture.
Solution: Create a structured Public Key Infrastructure (PKI):
- Keep root CAs offline for maximum security
- Use intermediate CAs for day-to-day certificate issuance
- Maintain separate CAs for different environments
- Implement strict controls on who can issue certificates
- Regularly update CA bundles to ensure continuous trust validation
4. Performance Considerations
Challenge: Implementing mTLS introduces additional computational load. The cryptographic operations required during TLS handshakes consume processing power, particularly under high connection volumes or with resource-constrained devices.
Solution: Optimize your infrastructure for mTLS performance:
- Evaluate hardware capabilities before deployment
- Consider specialized cryptographic hardware accelerators for high-volume environments
- Use session resumption techniques to reduce handshake overhead
- Implement connection pooling where appropriate
5. Implementation Strategy
When deploying mTLS across your infrastructure, a phased approach often works best:
- Start with permissive mode: Configure systems to accept both mTLS and plain traffic initially. This prevents service disruptions during transition and allows you to monitor adoption and troubleshoot issues.
- Monitor connection patterns: Use observability tools to verify which services successfully communicate via mTLS.
- Gradually enforce strict mode: Once services reliably support mTLS, enable the strict mode that rejects non-mTLS connections. Begin with less critical services and move to critical infrastructure only after thorough testing.
- Automate everything possible: Manual certificate management isn’t just cumbersome, it’s risky. Integrate certificate management into your CI/CD pipeline, use platforms that automatically handle certificate rotation, and implement certificate expiration monitoring.
When Not to Use mTLS: Understanding the Limitations
While mutual TLS provides excellent security for many scenarios, it isn’t appropriate for every situation. Recognizing when mTLS might create more problems than it solves helps you deploy it strategically rather than universally.
- Public-Facing Websites. For standard public websites serving content to anonymous visitors, implementing mTLS creates significant barriers. Most users wouldn’t have client certificates, and the logistics of issuing certificates to potentially millions of visitors become impractical. In these cases, conventional TLS combined with application-level authentication methods (like passwords or OAuth) makes more sense.
- Consumer Applications. Applications targeting general consumers typically shouldn’t require mTLS. The technical complexity of installing and managing certificates overwhelms most non-technical users, leading to frustration and support issues. The degradation of user experience often outweighs the security benefits of consumer-facing services.
- Environments with Limited Certificate Management Capabilities. Organizations without a robust certificate lifecycle management infrastructure may struggle with mTLS implementation. Without automation for certificate provisioning, renewal, and revocation, the operational burden becomes unsustainable as systems scale. Starting with more straightforward security measures while building certificate management capabilities in these environments often proves more effective.
- Performance-Critical Systems with High Connection Volumes. For systems processing thousands of new connections per second, the added computational overhead of mutual certificate verification might impact performance. In these high-throughput scenarios, you may need to carefully evaluate whether the security benefits justify the additional latency and resource requirements.
Take Your Security to the Next Level with SSL Dragon
Ready to implement mTLS and strengthen your organization’s security posture? SSL Dragon offers the perfect starting point with our comprehensive range of SSL certificates from trusted Certificate Authorities.
Our team of security experts can guide you through selecting the proper certificates for your mTLS implementation, whether you’re securing microservices, APIs, or B2B communications.
Visit SSL Dragon today to explore our certificate offerings and take advantage of our competitive pricing, straightforward validation process, and responsive customer support—everything you need to start your mTLS journey.
Save 10% on SSL Certificates when ordering from SSL Dragon today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10






